What To Know
- The report uses the example of an Outlook phishing email with the subject line “[Action Required] Final Reminder – Verify your OWA Account now” to illustrate how a user could be tricked into visiting a fake Outlook website and giving away their login information.
- “They give cybercriminals the opportunity to leverage the reputation of trusted brands to give users a false sense of security that can be exploited to steal personal or commercial information for financial gain.
Editor’s brief: Phishing is getting more rampant, with some brands hitting the top of the list for scammers attempting to trick consumers into divulging their personal and access details. For example, brands such as DHL are frequently imitated by scammers in phishing attempts, since many consumers do purchase products from overseas and tracking their purchases is common. Check Point Software’s Brand Phishing Report for Q2 2022 lists the top brands being faked. Read more below.
SINGAPORE – Check Point Research (CPR), the Threat Intelligence arm of Check Point® Software Technologies Ltd. (NASDAQ: CHKP) and a leading provider of cyber security solutions globally, has published its Brand Phishing Report for Q2 2022. The report highlights the brands that were most frequently imitated by cybercriminals in their attempts to steal individuals’ personal information or payment credentials over the quarter.
After breaking into the top five most imitated brands in Q1, social media platform LinkedIn maintained its position as the industry standard. While Facebook’s share has decreased from 52% in Q1 to 45% in Q2 of all phishing attempts, this worrying trend still highlights the ongoing risks facing users of the trusted social media platform. Generally speaking, social networks remain the most imitated category, followed by technology, which this quarter surpassed shipping to become the most imitated sector.
Microsoft saw the most dramatic increase, with 13% of all brand phishing attempts, more than doubling from the previous quarter and displacing DHL from third place, which had 12%. Researchers will be keeping a close eye on the progress of brands like Adidas, Adobe, and HSBC in Q3 after breaking into the top 10 for the first time.
Increased Microsoft-related phishing attempts pose a risk to both individuals and businesses. Your Outlook email account isn’t the only thing at risk if a hacker obtains your login information; they’ll also have access to all the other services that use your account as a backend. The report uses the example of an Outlook phishing email with the subject line “[Action Required] Final Reminder – Verify your OWA Account now” to illustrate how a user could be tricked into visiting a fake Outlook website and giving away their login information.
Subject lines such as “You appeared in 8 searches this week,” “You have one new message,” and “I’d like to do business with you via LinkedIn” are examples of LinkedIn phishing emails that mimic the platform’s professional tone. Although it looked like it came from LinkedIn, the sender actually used an address that had nothing to do with the company.
As online shopping continues to rise in popularity, it is not surprising that 12% of all phishing attacks in Q2 used a fake DHL website. The report describes one such phishing scam in which consumers are duped into clicking on a malicious link in an email with the subject line “Incoming Shipment Notification.”
“Phishing emails are a prominent tool in every hacker’s arsenal as they are fast to deploy and can target millions of users at relatively low cost,” said Omer Dembinsky, Data Research Group Manager at Check Point Software. “They give cybercriminals the opportunity to leverage the reputation of trusted brands to give users a false sense of security that can be exploited to steal personal or commercial information for financial gain.
“The criminals will use any brand with sufficient reach and consumer trust. Hence, we see hackers expanding their activities with the first appearance of Adidas, Adobe, and HSBC in the top 10. The hackers trade on our trust in these brands and that very human instinct for ‘the deal.’ There’s a reason the hackers continue to use brand-based phishing. It works. So, consumers need to act with caution and look out for tell-tale signs of the fake email, like poor grammar, spelling mistakes or strange domain names. If in doubt, head for the brand’s own website rather than clicking any links.”
Brand phishing attacks prey on consumers’ trust in well-known companies by using the company’s logo and other recognizable brand elements in their own websites’ URLs. They also appeal to basic human emotions like the desire to avoid missing out on a deal. Customers feel pressured into acting quickly, even if they haven’t verified that the email really comes from the brand they think it does. As a result, they risk unwittingly downloading malicious software or disclosing sensitive personal information that could give cybercriminals access to their entire online life and even cause them financial harm.
Top phishing brands in Q2 2022
Below are the top brands ranked by their overall appearance in brand phishing attempts:
- LinkedIn (45%)
- Microsoft (13%)
- DHL (12%)
- Amazon (9%)
- Apple (3%)
- Adidas (2%)
- Google (1%)
- Netflix (1%)
- Adobe (1%)
- HSBC (1%)
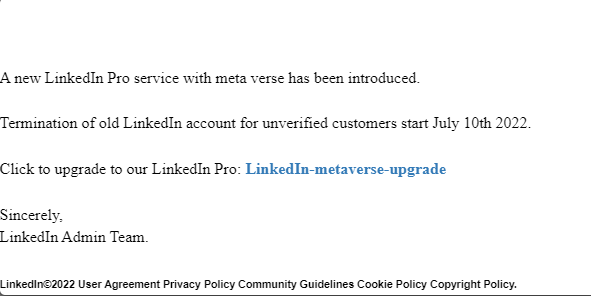
LinkedIn Phishing Email- Account Theft Example
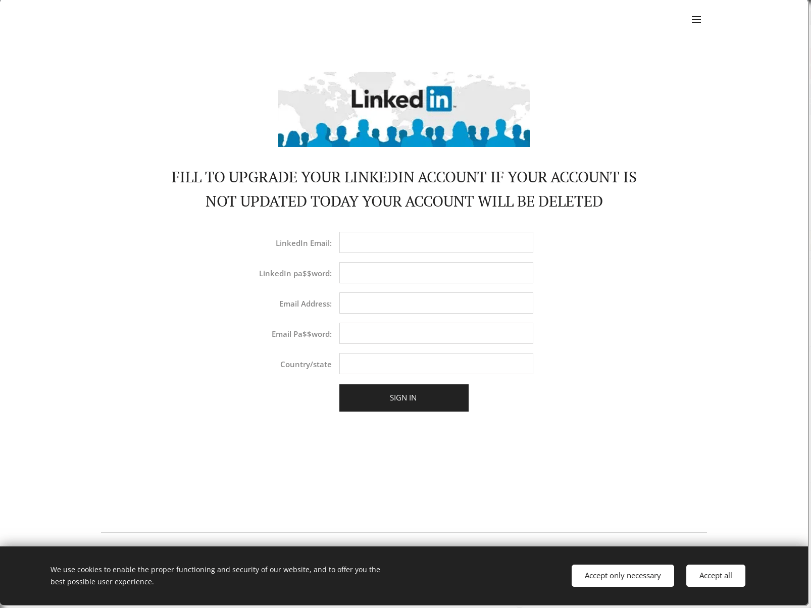
During the Q2 of 2022, we observed a malicious phishing email that used LinkedIn’s branding. The phishing email was sent from a webmail address and spoofed to appear as if it was sent from “LinkedIn Security”. The email contained the subject “LinkedIn Notice!!!”, and the content (see Figure 1) tries to entice the victim to click on a malicious link under the guise of updating their LinkedIn account version. This click will lead to the link, where the victim is then required to enter their LinkedIn account information (see Figure 2).
DHL Phishing Email – Account Theft Example
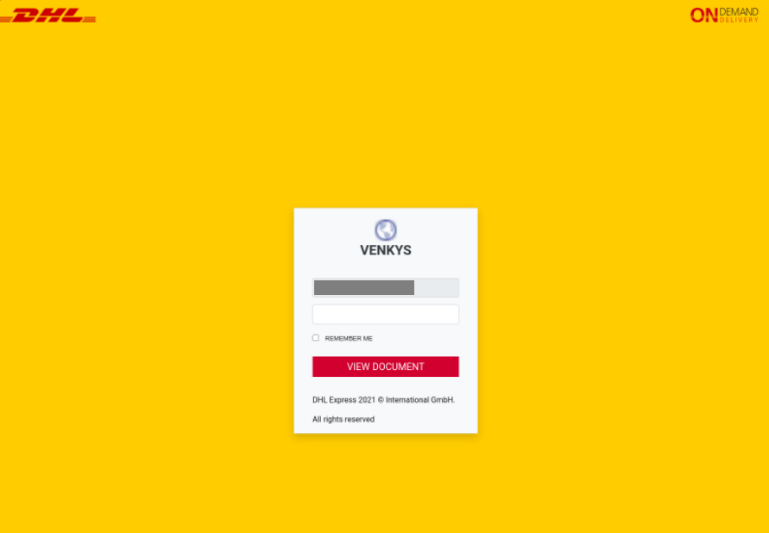
During the second quarter of 2022, we observed a malicious phishing email that used DHL’s branding. The phishing email was sent from a webmail address and spoofed to appear as if it was sent from “DHL EXPRESS”. The email contained the subject line “Incoming Shipment Notification”,and the content (see Figure 3) tries to persuade the victim to click on a malicious link. The victim is then required to enter their username and password.

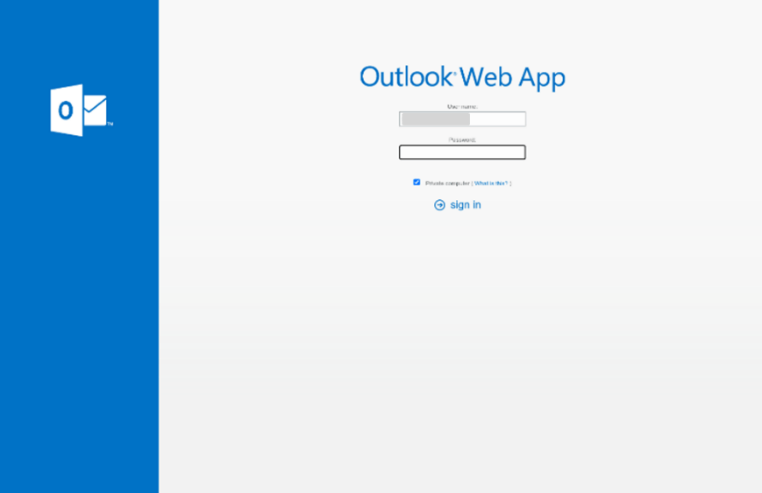
Outlook Phishing Email – Account Theft Example
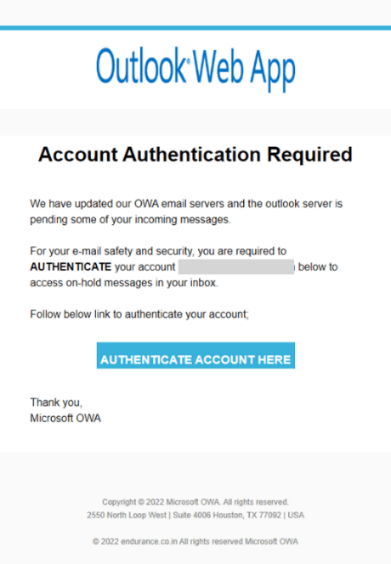
In this phishing email, we see an attempt to steal a user’s Outlook account information. The email (see Figure 5) which was sent from the email address “Outlook OWA”, contained the subject line “[Action Required] Final Reminder – Verify your OWA Account now”. The attacker was trying to lure the victim to click on a malicious link, which redirects the user to a fraudulent Outlook web app login page (see Figure 6). In the malicious link, the user needed to enter their username and password.
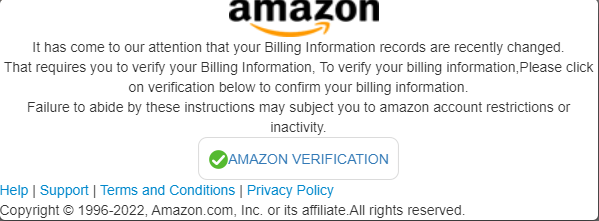
Amazon Phishing Email – Billing Information Theft Example
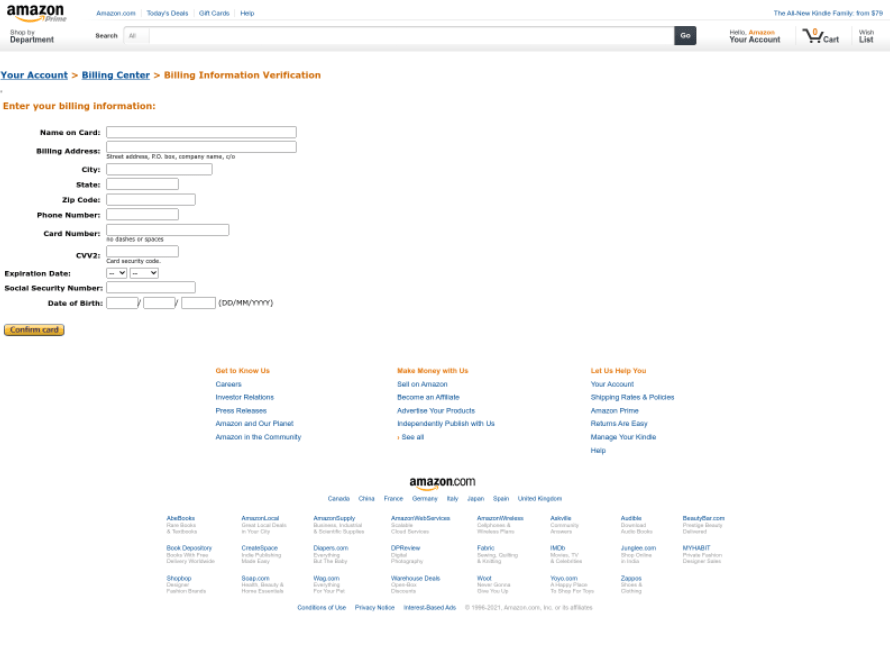
In this phishing email, we see an attempt to steal a user’s billing information. The email (see Figure 7) which was sent from the email address “Amazon”, contained the subject line “Your amazon account verification”. The title of the email and its contents are an attempt by the attacker to entice the victim to click on a malicious link, which redirects the user to a fraudulent page asking to enter billing information (see Figure 8).
###




